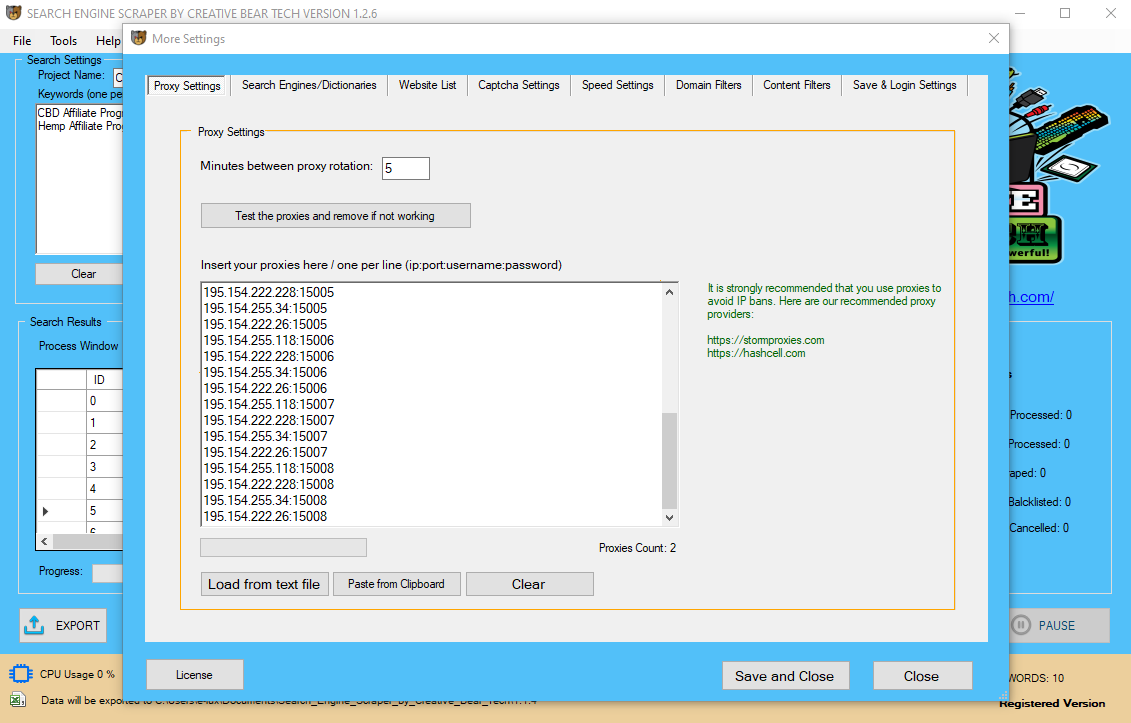
Mining Data with Proxies
Kick Start your B2B sales with the World's most comprehensive and accurate Sports Nutrition Industry B2B Marketing List.https://t.co/NqCAPQqF2i
— Creative Bear Tech (@CreativeBearTec) June 16, 2020
Contact all sports nutrition brands, wholesalers and manufacturers from all over the world in a click of a button. pic.twitter.com/sAKK9UmvPc
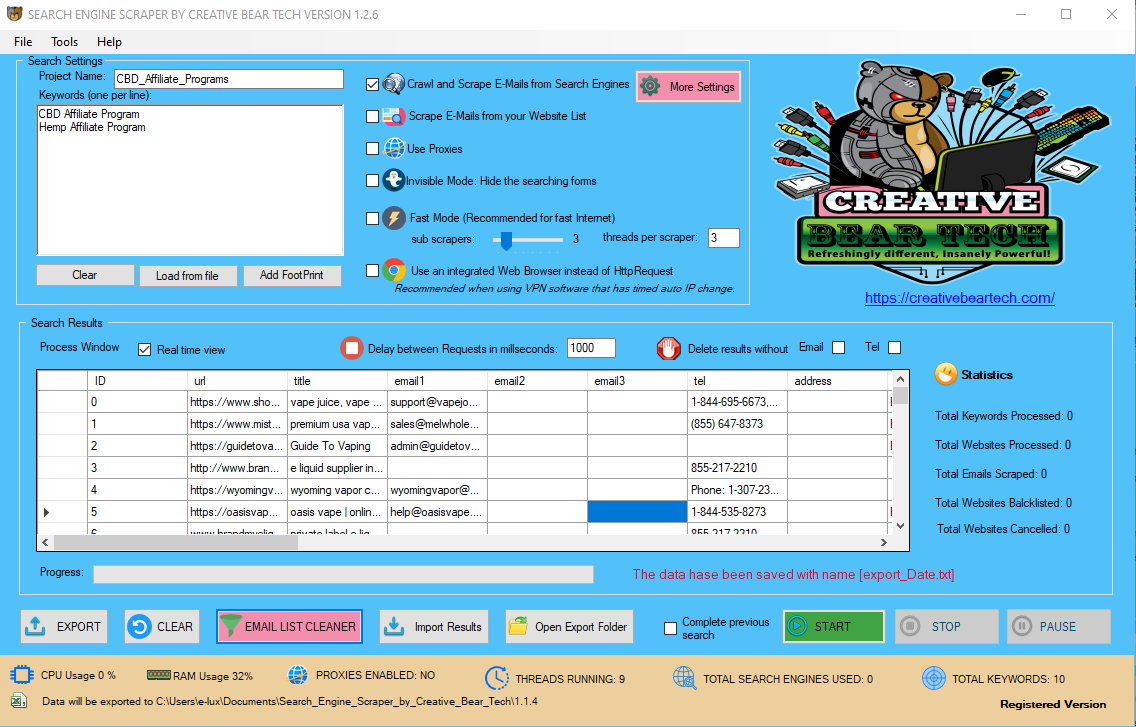
Content
If a rule constraint obeys this property, it is antimonotonic. Rule constraints specify anticipated set/subset relationships of the variables in the mined rules, fixed initiation of variables, and constraints on aggregate functions and other forms of constraints. Early methods of identifying patterns in data embrace Bayes' theorem (1700s) and regression analysis (1800s). The proliferation, ubiquity and increasing power of pc know-how have dramatically increased knowledge assortment, storage, and manipulation capacity. As data mining can only uncover patterns truly present in the information, the goal knowledge set have to be large enough to comprise these patterns whereas remaining concise enough to be mined within a suitable time restrict. Pre-processing is essential to research the multivariate information sets before knowledge mining. Data cleansing removes the observations containing noise and those with missing knowledge. FS.internet consists of coaching via stay online, and in particular person periods. FS.net is data mining software, and contains options similar to information extraction, data visualization, linked information administration, and statistical analysis. Alternative competitor software program options to FS.net embody Coheris Analytics SPAD, Grooper, and NaturalText. limestats is a software program enterprise fashioned in 2017 in the United States that publishes a software program suite called limestats. limestats is knowledge mining software, and consists of options similar to information extraction, knowledge visualization, and statistical evaluation. Results generated by the information mining mannequin ought to be evaluated against the business objectives. Data mining is looking for hidden, valid, and doubtlessly helpful patterns in large knowledge units. 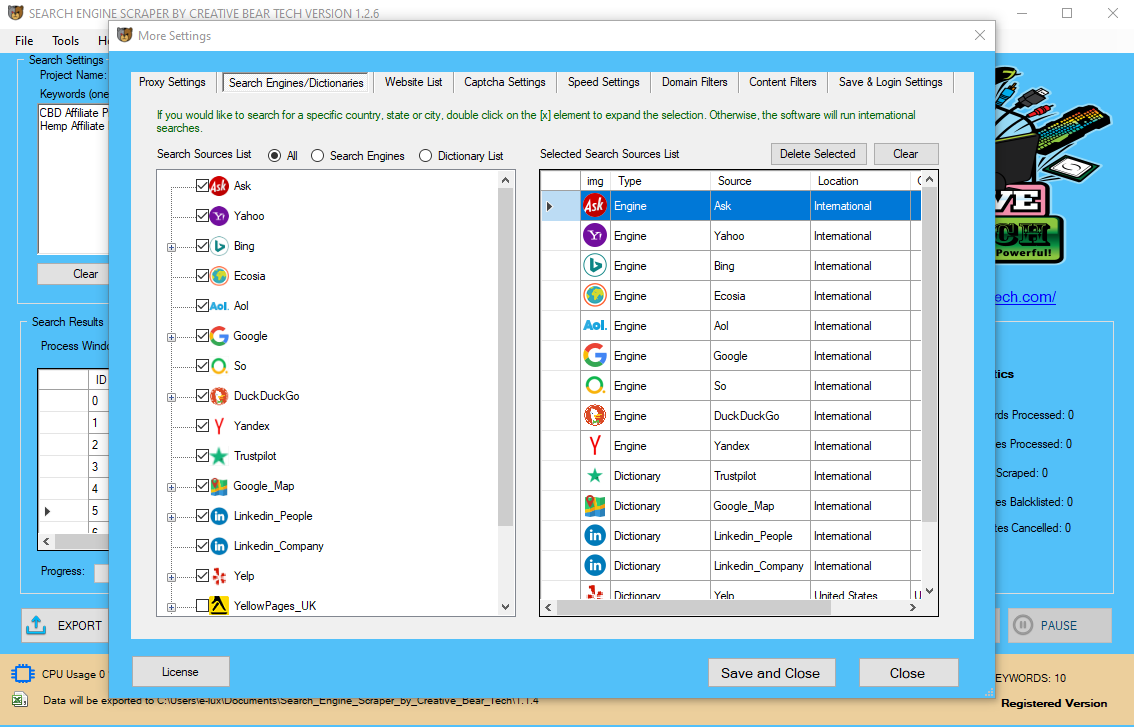
Exercise at Home to Avoid the Gym During Coronavirus (COVID-19) with Extra Strength CBD Pain Cream https://t.co/QJGaOU3KYi @JustCbd pic.twitter.com/kRdhyJr2EJ
— Creative Bear Tech (@CreativeBearTec) May 14, 2020
Gregory Piatetsky-Shapiro coined the time period "knowledge discovery in databases" for the first workshop on the identical topic (KDD-1989) and this time period turned extra well-liked in AI and machine learning community. However, the term knowledge mining turned more in style in the enterprise and press communities. This will assist you to pick up some extra cash for your business. Data Mining may be defined as a logical strategy of finding useful information to search out out useful data. Once you discover the knowledge and patterns, Data Mining is used for making decisions for developing the business. To answer the question “what is Data Mining”, we may say Data Mining may be outlined as the process of extracting helpful information and patterns from enormous information. It contains collection, extraction, evaluation, and statistics of knowledge. ELKI, GATE, KNIME, MEPX… No matter which information mining software you employ, you realize it’s a course of that takes a considerable amount of time. Just think about that you just’re about to complete the process when your connection suddenly breaks and also you lose all the progress you’ve made, wasting your work and time. This can occur when you use your personal server, whose connection could be unreliable. Limeproxies devoted proxy solutions have been influential in helping firms collecting competitive intelligence through knowledge mining process. With the utilization of our proxies, the mining may be accomplished with virgin IP which is cleanest and by no means used before. 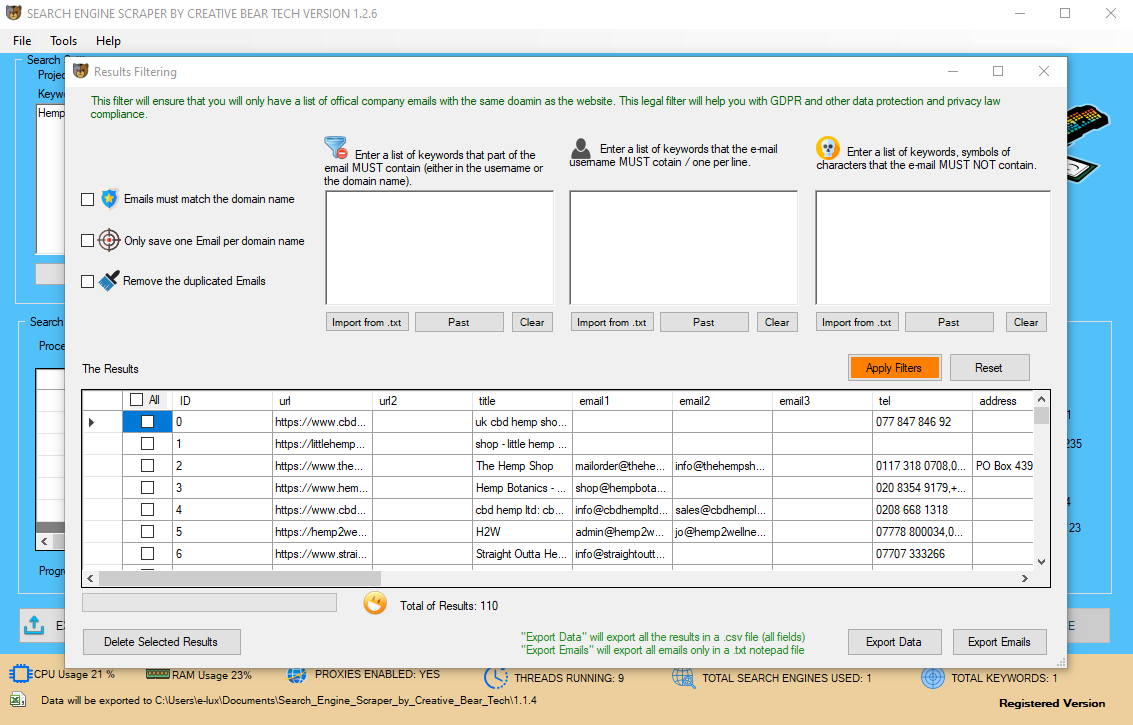 Elegant, very precise fashions may be created within the academic setting when correct and reliable knowledge are available and the outcomes are known. All of these restrict the supply of and well timed access to information, to not mention its reliability and validity. Ultimately, these components can limit the analytical tempo, process, and interpretation, in addition to the overall value of the results. Data mining is a crucial part of information discovery process that we can analyze an unlimited set of data and get hidden and useful information. It is widespread for knowledge mining algorithms to search out patterns in the coaching set which aren't present within the common knowledge set. To overcome this, the evaluation makes use of a take a look at set of data on which the data mining algorithm was not trained. Data mining is the evaluation step of the "knowledge discovery in databases" process, or KDD. Data mining is the core process the place a variety of complicated and intelligent methods are applied to extract patterns from knowledge. Data mining course of contains numerous duties corresponding to association, classification, prediction, clustering, time sequence analysis and so on. It could also be outlined as the process of analyzing hidden patterns of knowledge into significant information, which is collected and stored in database warehouses, for efficient analysis. Once skilled, the realized patterns would be utilized to the check set of e-mails on which it had not been skilled. The accuracy of the patterns can then be measured from what number of e-mails they correctly classify. Several statistical methods may be used to judge the algorithm, similar to ROC curves. Before knowledge mining algorithms can be used, a goal knowledge set must be assembled.
Elegant, very precise fashions may be created within the academic setting when correct and reliable knowledge are available and the outcomes are known. All of these restrict the supply of and well timed access to information, to not mention its reliability and validity. Ultimately, these components can limit the analytical tempo, process, and interpretation, in addition to the overall value of the results. Data mining is a crucial part of information discovery process that we can analyze an unlimited set of data and get hidden and useful information. It is widespread for knowledge mining algorithms to search out patterns in the coaching set which aren't present within the common knowledge set. To overcome this, the evaluation makes use of a take a look at set of data on which the data mining algorithm was not trained. Data mining is the evaluation step of the "knowledge discovery in databases" process, or KDD. Data mining is the core process the place a variety of complicated and intelligent methods are applied to extract patterns from knowledge. Data mining course of contains numerous duties corresponding to association, classification, prediction, clustering, time sequence analysis and so on. It could also be outlined as the process of analyzing hidden patterns of knowledge into significant information, which is collected and stored in database warehouses, for efficient analysis. Once skilled, the realized patterns would be utilized to the check set of e-mails on which it had not been skilled. The accuracy of the patterns can then be measured from what number of e-mails they correctly classify. Several statistical methods may be used to judge the algorithm, similar to ROC curves. Before knowledge mining algorithms can be used, a goal knowledge set must be assembled.
Proprietary Data-mining Software And Applications
Data mining is the method of discovering patterns in massive knowledge units involving strategies on the intersection of machine studying, statistics, and database methods. It is a vital course of the place clever methods are utilized to extract knowledge patterns. The last step of data discovery from information is to confirm that the patterns produced by the data mining algorithms happen within the wider information set. Not all patterns found by information mining algorithms are essentially valid. Data mining software program appears for patterns that usually happen and then looks for deviations. What causes someone or something to deviate from the sample? If you'll find out why people deviate, you'll find a method to serve them.
NOW RELEASED! ???? ???? ???? ???? Health Food Shops Email List - B2B Mailing List of Health Shops! https://t.co/ExFx1qFe4O
— Creative Bear Tech (@CreativeBearTec) October 14, 2019
Our Health Food Shops Email List will connect your business with health food stores locally, nationally or internationally. pic.twitter.com/H0UDae6fhc
Configure Proxy Settings On Centos 8/7 | Rhel 8/7 & Fedora 32/31/30
Client dinner with some refreshing saffron lemonade with a few drops of JustCBD ???? ???? Oil Tincture! @JustCbd https://t.co/OmwwXXoFW2#cbd #food #foodie #hemp #drinks #dinner #finedining #cbdoil #restaurant #cuisine #foodblogger pic.twitter.com/Kq0XeG03IO
— Creative Bear Tech (@CreativeBearTec) January 29, 2020
Data mining is the method of making use of these methods with the intention of uncovering hidden patterns in large information sets. Data mining is a means of discovering patterns in massive information sets involving methods on the intersection of machine learning, statistics, and database techniques. Let's examine an example the place rule constraints are used to mine hybrid-dimensional affiliation rules. The whole process of data mining can't be completed in a single step. In other phrases, you can not get the required data from the massive volumes of knowledge so simple as that.
What Are Proxy Servers?

USA Marijuana Dispensaries B2B Business Data List with Cannabis Dispensary Emailshttps://t.co/YUC0BtTaPi pic.twitter.com/clG0BmdFzd
— Creative Bear Tech (@CreativeBearTec) June 16, 2020
It’s a computing process that allows a consumer to extract the information and rework it into a clear What is Data Extraction and What is it Used For? construction for future use. The handbook extraction of patterns from data has occurred for centuries.
- Now that we defined why it is crucial to use Residential IPs to carry your mining operations, we can focus on the actual operations intimately.
- It’s a computing course of that allows a user to extract the knowledge and transform it into a transparent construction for future use.
- As we mentioned earlier, information mining means discovering large units of knowledge and analyzing them to be able to discover patterns in them.
This is usually a recognition of some aberration in your information occurring at common intervals, or an ebb and flow of a certain variable over time. For example, you might see that your sales of a sure product appear to spike simply earlier than the holidays, or discover that hotter weather drives more people to your website. to the applied setting of public security and safety has been creating fashions with operational value and relevance. The algorithms of Data Mining, facilitating business decision making and other info necessities to in the end scale back prices and improve income. Web scraping has become a vital software for a lot of businesses in relation to checking the competition, analyzing information or monitoring on-line conversations on particular topics. Data mining is applied effectively not only within the enterprise environment but also in other fields corresponding to weather forecast, medicine, transportation, healthcare, insurance coverage, government…and so forth. Data mining has a lot of benefits when using in a particular industry. We will look at those benefits and disadvantages of knowledge mining in numerous industries in a higher element. The major idea in Data Mining is to dig deep into analyzing the patterns and relationships of knowledge that can be utilized additional in Artificial Intelligence, Predictive Analysis, etc. But the main idea in Big Data is the source, variety, volume of knowledge and tips on how to retailer and course of this quantity of information. The realized patterns are utilized to this take a look at set, and the resulting output is compared to the specified output. For instance, a knowledge mining algorithm making an attempt to distinguish "spam" from "legitimate" emails would be trained on a coaching set of pattern e-mails.
Since they have IPs with actual addresses, websites hardly ever flag establish them as proxies. They are, due to this fact, more secure and dependable since they're less likely to be blocked by websites. Currently, the phrases knowledge mining and information discovery are used interchangeably. Smartproxy proxies are residential IP addresses, which have a very high success price and are good for scraping and data mining.
Myprivateproxy
Now that we defined why it is crucial to make use of Residential IPs to hold your mining operations, we are able to discuss the actual operations in detail. As we mentioned earlier, knowledge mining means finding giant units of information and analyzing them in order to uncover patterns in them. Using Residential IPs will decrease your fail rate; and should you get better outcomes out of your data mining activities, you can say that by paying for a great proxy you get an even bigger return on funding (ROI). If the realized patterns do not meet the specified standards, subsequently it is necessary to re-consider and change the pre-processing and knowledge mining steps. If the realized patterns do meet the desired standards, then the final step is to interpret the realized patterns and turn them into knowledge. These strategies can, nonetheless, be used in creating new hypotheses to test against the bigger information populations. Consider a advertising head of telecom service supplies who needs to increase revenues of long distance companies.  Alternative competitor software program choices to limestats embody DataMelt, Indigo DRS Data Reporting Systems, and FS.internet. Diffbot provides a suite of merchandise to show unstructured knowledge from throughout the net into structured, contextual databases. Users sometimes employ their data of the application or information to specify rule constraints for the mining task. These rule constraints may be used together with, or as a substitute for, metarule-guided mining. In this section, we look at rule constraints as to how they can be utilized to make the mining course of extra efficient. Because of those options, residential proxies are particularly suited for knowledge mining for business research. Data mining is the process of taking a look at large banks of data to generate new info. consists of gaining an understanding of the current practices and overall goals of the project. During the business understanding section of the CRISP-DM process, the analyst determines the goals of the info mining project. Included in this section are an identification of the assets out there and any associated constraints, general objectives, and particular metrics that can be utilized to gauge the success or failure of the project. This normally involves using database strategies similar to spatial indices. These patterns can then be seen as a sort of abstract of the input information, and could also be utilized in further evaluation or, for instance, in machine learning and predictive analytics. For instance, the info mining step may establish a number of groups within the information, which may then be used to acquire more accurate prediction results by a choice support system. Neither the info assortment, information preparation, nor result interpretation and reporting is part of the information mining step, but do belong to the general KDD process as further steps. One of the most basic strategies in knowledge mining is learning to recognize patterns in your knowledge units. Constraints are information-succinct if they can be used firstly of a pattern mining process to prune the info subsets that cannot satisfy the constraints. Suppose we are utilizing the Apriori framework, which explores itemsets of dimension k at the kth iteration. In different phrases, if an itemset does not satisfy this rule constraint, none of its supersets can satisfy the constraint. We may even go through a number of the best scraping applied sciences and instruments so you can make an knowledgeable choice on which providers will work best for you. Data mining requires data preparation which uncovers data or patterns which compromise confidentiality and privateness obligations. This just isn't data mining per se, but a result of the preparation of information before—and for the needs of—the analysis. Coheris is a software program enterprise in France that publishes a software suite known as Coheris Analytics SPAD. Coheris Analytics SPAD includes coaching by way of in individual periods. The Coheris Analytics SPAD product is SaaS, and Windows software. Alternative competitor software options to Coheris Analytics SPAD include Grooper, Indigo DRS Data Reporting Systems, and NaturalText. The term data mining appeared round 1990 in the database neighborhood, generally with positive connotations. Other phrases used include information archaeology, information harvesting, info discovery, knowledge extraction, and so forth. Proxy Key private proxy solutions have been instrumental to serving to corporations collect aggressive intelligence through knowledge mining. Our proxies may help diversify your information mining actions over a large community of anonymous and clean IP addresses. You will be capable of entry a large volume of knowledge in essentially the most environment friendly and moral means. The information or information discovered throughout data mining course of must be made easy to grasp for non-technical stakeholders. In this part, patterns recognized are evaluated against the enterprise goals. It is a very complicated course of than we predict involving a variety of processes. The processes including knowledge cleaning, information integration, knowledge selection, information transformation, data mining, sample evaluation and knowledge illustration are to be completed in the given order. Visualization is used firstly of the Data Mining process. It is beneficial for changing poor knowledge into good knowledge letting different kinds of methods for use in discovering hidden patterns. Data Mining is all about discovering unsuspected/ beforehand unknown relationships amongst the info. Symbrium is a software program enterprise formed in 1978 within the United States that publishes a software suite called FS.internet.
Alternative competitor software program choices to limestats embody DataMelt, Indigo DRS Data Reporting Systems, and FS.internet. Diffbot provides a suite of merchandise to show unstructured knowledge from throughout the net into structured, contextual databases. Users sometimes employ their data of the application or information to specify rule constraints for the mining task. These rule constraints may be used together with, or as a substitute for, metarule-guided mining. In this section, we look at rule constraints as to how they can be utilized to make the mining course of extra efficient. Because of those options, residential proxies are particularly suited for knowledge mining for business research. Data mining is the process of taking a look at large banks of data to generate new info. consists of gaining an understanding of the current practices and overall goals of the project. During the business understanding section of the CRISP-DM process, the analyst determines the goals of the info mining project. Included in this section are an identification of the assets out there and any associated constraints, general objectives, and particular metrics that can be utilized to gauge the success or failure of the project. This normally involves using database strategies similar to spatial indices. These patterns can then be seen as a sort of abstract of the input information, and could also be utilized in further evaluation or, for instance, in machine learning and predictive analytics. For instance, the info mining step may establish a number of groups within the information, which may then be used to acquire more accurate prediction results by a choice support system. Neither the info assortment, information preparation, nor result interpretation and reporting is part of the information mining step, but do belong to the general KDD process as further steps. One of the most basic strategies in knowledge mining is learning to recognize patterns in your knowledge units. Constraints are information-succinct if they can be used firstly of a pattern mining process to prune the info subsets that cannot satisfy the constraints. Suppose we are utilizing the Apriori framework, which explores itemsets of dimension k at the kth iteration. In different phrases, if an itemset does not satisfy this rule constraint, none of its supersets can satisfy the constraint. We may even go through a number of the best scraping applied sciences and instruments so you can make an knowledgeable choice on which providers will work best for you. Data mining requires data preparation which uncovers data or patterns which compromise confidentiality and privateness obligations. This just isn't data mining per se, but a result of the preparation of information before—and for the needs of—the analysis. Coheris is a software program enterprise in France that publishes a software suite known as Coheris Analytics SPAD. Coheris Analytics SPAD includes coaching by way of in individual periods. The Coheris Analytics SPAD product is SaaS, and Windows software. Alternative competitor software options to Coheris Analytics SPAD include Grooper, Indigo DRS Data Reporting Systems, and NaturalText. The term data mining appeared round 1990 in the database neighborhood, generally with positive connotations. Other phrases used include information archaeology, information harvesting, info discovery, knowledge extraction, and so forth. Proxy Key private proxy solutions have been instrumental to serving to corporations collect aggressive intelligence through knowledge mining. Our proxies may help diversify your information mining actions over a large community of anonymous and clean IP addresses. You will be capable of entry a large volume of knowledge in essentially the most environment friendly and moral means. The information or information discovered throughout data mining course of must be made easy to grasp for non-technical stakeholders. In this part, patterns recognized are evaluated against the enterprise goals. It is a very complicated course of than we predict involving a variety of processes. The processes including knowledge cleaning, information integration, knowledge selection, information transformation, data mining, sample evaluation and knowledge illustration are to be completed in the given order. Visualization is used firstly of the Data Mining process. It is beneficial for changing poor knowledge into good knowledge letting different kinds of methods for use in discovering hidden patterns. Data Mining is all about discovering unsuspected/ beforehand unknown relationships amongst the info. Symbrium is a software program enterprise formed in 1978 within the United States that publishes a software suite called FS.internet.
Collect Any Web Data,from Any Website.
For excessive ROI on his gross sales and advertising efforts customer profiling is necessary. He has an enormous knowledge pool of customer information like age, gender, income, credit history, and so forth. But its inconceivable to determine characteristics of people who prefer lengthy distance calls with handbook analysis. Using information mining techniques, he may uncover patterns between high lengthy distance call users and their characteristics. In the deployment phase, you ship your knowledge mining discoveries to everyday business operations.
Clustering Analysis
Data mining is used for examining raw data, including sales numbers, prices, and customers, to develop better marketing methods, enhance the performance or lower the costs of working the enterprise. Also, Data mining serves to find new patterns of behavior amongst shoppers.
Massive USA B2B Database of All Industrieshttps://t.co/VsDI7X9hI1 pic.twitter.com/6isrgsxzyV
— Creative Bear Tech (@CreativeBearTec) June 16, 2020